Digital Interruption is lucky enough to have a penetration testing team which consists of experienced hackers and penetration testers. This means we often have the pleasure of experimenting with attacks and demonstrating weaknesses that might otherwise only be seen as theoretical attacks. One great example of this is TEMPEST – also known as Van Eck Phreaking. In this blog post, we’ll see TEMPEST in action and try and help you understand whether this is an attack you should worry about.
What is TEMPEST?
First, some background. TEMPEST is an attack that has been known about as early as the 70’s and brought to public attention by Wim van Eck in the mid 80’s. TEMPEST is a technique an attacker can use to remotely spy on electronic devices using equipment to pick up side-band electromagnetic transmissions. This effectively means it’s possible to recover data about what the device is doing based on things such as the unintentional transmissions that most electronic devices will emit when in use. The reason why these transmissions exist is due to the nature of electromagnetism; as electricity (i.e. data) travels along a wire, it will emit a magnetic field. If this can be picked it and analysed, it may be possible to recover information about the data being processed.
Is it practical?
TEMPEST could be a security issue as almost every organisations uses many electronic devices that process data. This list would include things such as computers, tablets, phone and even monitors and keyboards. Each of these devices could be vulnerable to being spied on remotely. In the past these “side channel” attacks have been used to recover encryption keys, exfiltrate data from an air gapped network and view images displayed on screens.
To understand this attack, we wanted to see it in action and understand what the limitations were. Once we had this information, we’d be better able to advise our clients.
During our testing with TempestSDR, we were able to pick up and view an LCD monitor’s display from a few inches away. This may not sound like much but this is with off the shelf hardware (we used a HackRF SDR) that costs less than £300.
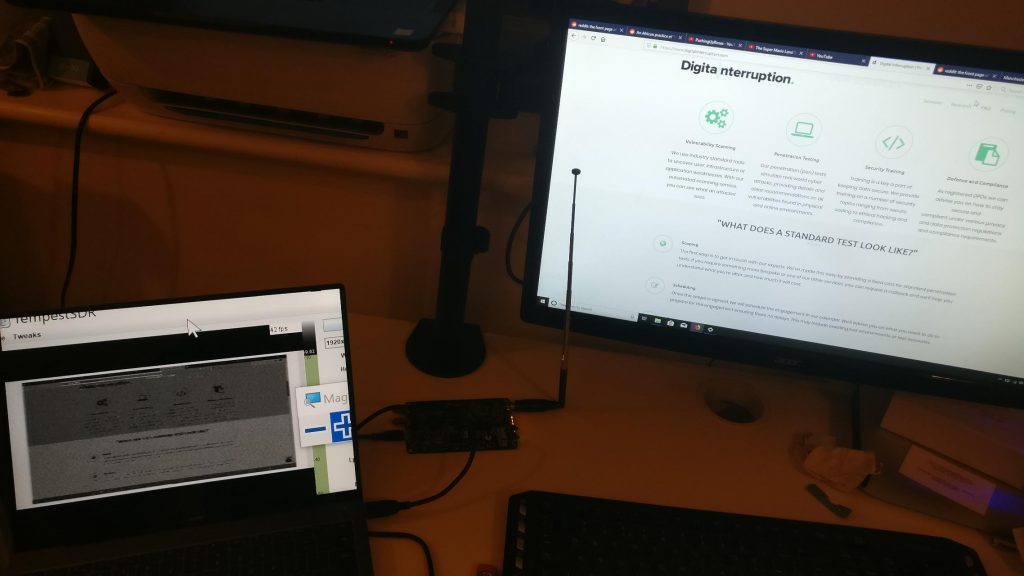
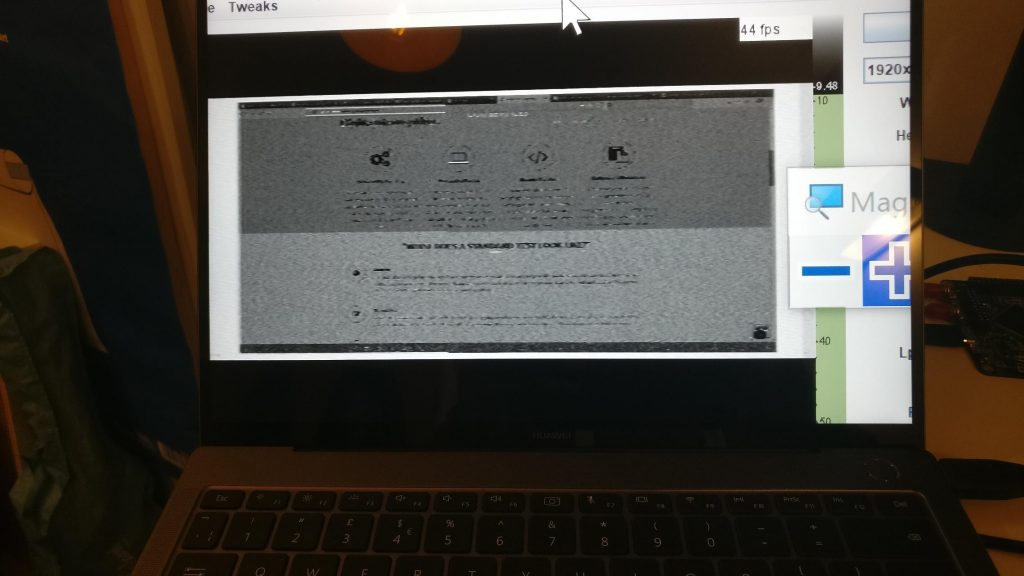
As can be seen above, it was possible to view the LCD display remotely, however there were two main limitations. The first being image clarity. With the image we recovered, it was possible to make a guess as to which web page was visited or application was used but it was not possible to read text or make out details. The second limitation was due to range. With our equipment, it was only possible to recover an image from about an inch away from the display. Together, this would make this type of attack impractical for many situations however it is likely that both limitations could be slightly improved with better hardware.
Defence
Should you be worried about this type of attack? Well, like a lot of things in security – it depends. In our opinion, most companies should not worry too much about this type of attack. There are often easier ways to view an employee’s screens or for an attacker to gain the information they’re after.
Where we see this attack being useful is when highly classified or sensitive data is being processed. As it was not possible to view a crisp image, an attacker would also be required to spy on a device that had a UI that made it easy to determine which specific actions were performed. A candidate that comes to mind for this type of attack is electronic voting systems. Outside of this, although the attack is novel, it’s unlikely to be the way an organsation is compromised. We’ll continue this research to try and understand whether it is easier to recover keystrokes from touchscreen keyboards due to the way each key is highlighted on touch.
The best protection against TEMPEST attacks is to block the signal. This can be done by placing highly sensitive equipment in Faraday cages so signals can not escape. In our experiments, lower quality equipment tended to be “noisier” and so easier to pick up transmissions and so more “premium” equipment may help protect against this attack.
Data Exfiltration with Tempest
Another interesting use of TEMPEST is data exfiltration. In our experiments we were able to implant malware that would blink the monitor black and white. This would cause as AM signal to be generated as the display displayed each colour. By monitoring the change in amplitude of the captured signal, it was possible to convert the black and white flashes back into a stream of bits. Although this is a slow process, it was possible to successfully transmit our test string. It is likely possible to improve this technique by encoding bits differently. For example, a more complex modulation scheme could encode several bits in a single frequency allowing many more bits to be transmitted in one time.
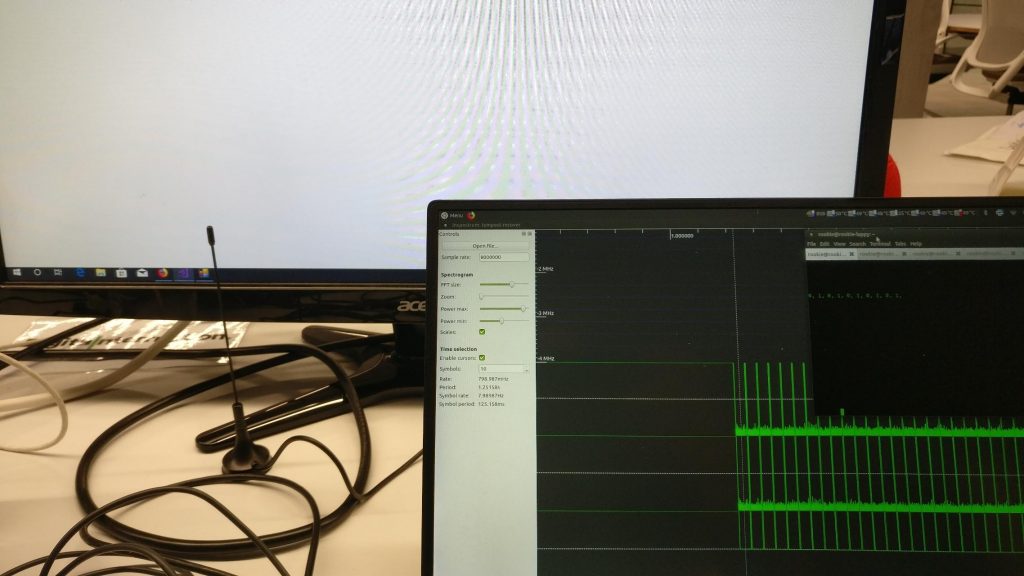
Using a cheap RTLSDR (a cost of roughly £15) we were able to recover data at several inches. We believe this can be improved and will be a future research task.
If you’re interested in our research, keep an eye on our research blog or get in contact if you’re interested in our offensive or defensive security services.

