This is something that was said to us by a small business owner who was worried their company and data wasn’t secure. To me, a statement like this means the infosec community has made it too difficult for small companies to take security into their own hands and be confident they’ve done it right. How do small companies become secure?
Now it’s certainly true that hackers can be scary. There is a strange “unknown” that goes with the idea that someone could be attacking your company, reading your emails or downloading your confidential source code.
I wanted to write this article to help companies in a similar situation to the company that we mentioned above. Hopefully after reading this, you will have a better understanding of why you should secure your company but more importantly, how to go about it.
The Threat
The first thing to understand is who is the threat? Not all companies are worried about the same type of attacker. For example, a small application development company or marketing agency probably doesn’t need to worry about being hacked by Nation States. A large bank might. I like to group attackers into the following types:
- Unsophisticated Attacker
- Disgruntled Employee
- Skilled Attacker
- Nation State Attacker
Am I really a target?
Unfortunately the answer is a definitive maybe. While it’s unlikely your company will be directly targeted, many attackers will scan the Internet for vulnerable systems or try to infect as many computers as possible with malware, usually via a malicious email. Once infected, the attacker might stop you from accessing your files until you pay the attacker’s fee. This is called ransomware. A recent example of this would be the WannaCry attack in May 2017.
- Unsophisticated Attacker
- Disgruntled Employee
- Skilled Attacker
- Nation State Attacker
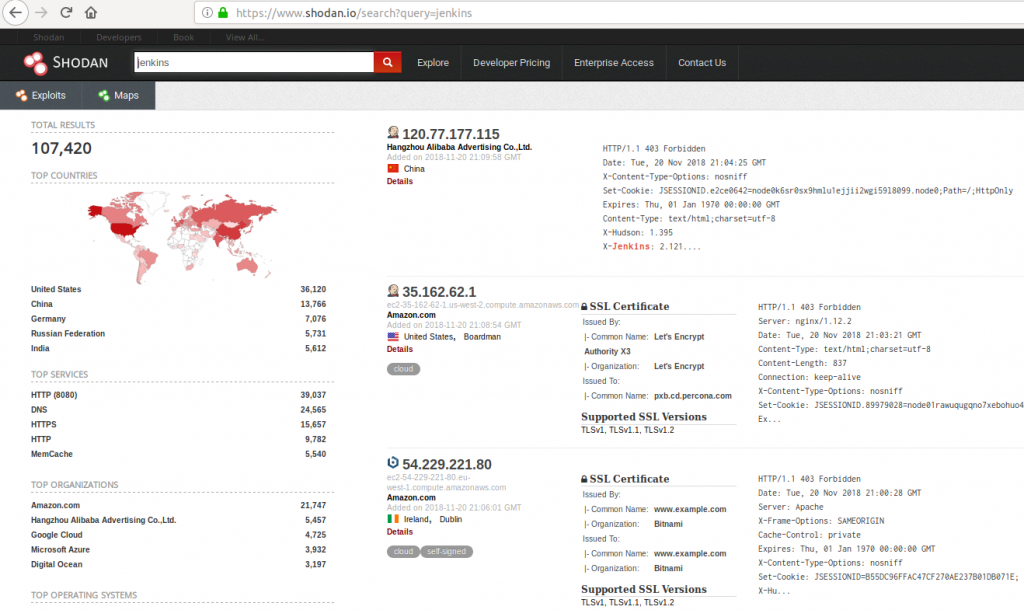
The screenshot above shows how easy it can be for an attacker to look for all instances of specific software. If your software is vulnerable and on that list, it will likely be attacked.
What this means is that an attacker might not be interested in Mrs Lovett’s Pie Shop, they may be interested in any vulnerable computer she has on the Internet or any data she’s holding about her customers such as usernames, passwords and credit card numbers.
Becoming Secure
Security isn’t free. Even taking out the cost of third party consultants, software etc there is also a cost involved with the time taken to get secure and to stay secure. To help decide what the budget should be, I think a good question to start with is “How much would I pay not to be in the news because I had a data breach?”. If the answer if £100, that’s good as it tells you something. If it’s £10,000, that’s even better. Although many companies are trying to sell security services (we’re no exception), it should be inline with what your risk appetite is. If you’re happy for your company to take more risk, then you may decide the security budget is better spent elsewhere. If you’re not so happy with that risk of a breach, the budget should be adjusted accordingly.
To help as many companies as possible, we suggest a tiered approach. Each step gets you more secure, but also will increase the amount of money spent.
Step 1 – A good baseline
Knowing where to start can be the hardest part so let’s make it easy. Look into a certification such as Cyber Essentials. Just like passing an MOT doesn’t mean your car won’t break down, no certification can make you secure. Cyber Essentials does allow you to easily check your company has the security controls in place to defect unsophisticated attackers. Getting Cyber Essentials means you have a level of protection where you can worry much less about low skilled hackers taking your company offline with known vulnerabilities. This can be important even if you use cloud providers as eventually, the data will be stored on your company computer/laptop/phone.
The Cyber Essentials Accreditation Bodies provides self assessment questionnaires where they aim to find out things such as password policy, the firewalls protecting your sensitive data and whether your devices have appropriate protection for malware. The actual Cyber Essentials accreditation is fairly cheap (~£300) but there may be cost involved with bringing in a consultant (we’d always recommend a certified Practitioner such as the consultants at Digital Interruption) for a few days to help test and configure your hosts and networks in preparation for accreditation.
For added peace of mind, Cyber Essentials Plus adds a vulnerability scan by a third party as part of the process.
Step 2 – Doing the right thing
Once a good baseline is met (possibly with Cyber Essentials) it is a good idea to define other security policies. These should define what is acceptable in the organisation and will likely include things such as how to protect/encrypt external storage, how to raise in incident, how to report a phishing email etc. These policies not only describe what “secure” looks like at your company, but it also helps you to further understand your threat. You may need support from consultants who specialise in this area to help you define you security policies, but bear in mind, a policy is only effective if it is enforced.
A strong security policy is also proof of your security intention which can help set your company apart from your competitors.
Step 3 – Keeping up to date with threats
For additional security, a continuous monitoring program would be a solid third step. This should include continuous vulnerability scanning of all your assets such as PCs, servers and web applications as well as monitoring malicious activities on the network such as by an Intrusion Detection System. Logs should be kept but more importantly a policy around log review should be developed and implemented.
Although this is unlikely to pick up highly targeted threats, it does let you easily detect when a new threat emerges. It’s important to keep in mind that security isn’t static. Being secure today does not mean you will be secure tomorrow as new exploits and techniques are being released almost daily.
Step 4 – Getting ahead
If you’ve completed steps 1-3, you may decide your company is happy knowing that you have appropriate security controls in place to either protect, detect or respond to a number of attacks. Good Job!
There are times however, when a company might need more assurance than this. For example, you develop a web application your customers use and you want to provide your customers assurance you’re not only protected against known exploits, but you’ve written your product in such a way as to be resilient to attack from skilled and targeted attackers.
In this case, it’s time to look at various attack simulation exercises, often known as penetration or pen testing. With penetration testing, an experienced “white hat hacker” will attempt to gain access to your application or infrastructure by using the skills they have developed over a number of years. There are different types of tests depending on your needs and we’ve outlined them in a previous post.
We also have other advice and guidance on how companies can take security into their own hands.
If you require help or advice on getting your company secure, get in touch. We can help you understand the best services for you with a no obligation call.

